What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2024-02-23 14:02:40 | La violation des données chez French Healthcare Payment Processor met 20 millions de titulaires de police en danger Data Breach at French Healthcare Payment Processor Puts 20 Million Policyholders at Risk (lien direct) |

|
Data Breach | ★★★ | ||
| 2024-01-30 14:00:00 | CyberheistNews Vol 14 # 05 Myth de la violation de données massive Éteinte: les gros titres masquent une menace mineure CyberheistNews Vol 14 #05 Myth of Massive Data Breach Busted: Big Headlines Mask a Minor Threat (lien direct) |

|
Data Breach Threat | ★★★ | ||
| 2024-01-23 21:21:14 | Alerte de cybersécurité sans précédent: 26 milliards d'enregistrements exposés dans une violation de données méga Unprecedented Cybersecurity Alert: 26 Billion Records Exposed in Mega Data Breach (lien direct) |
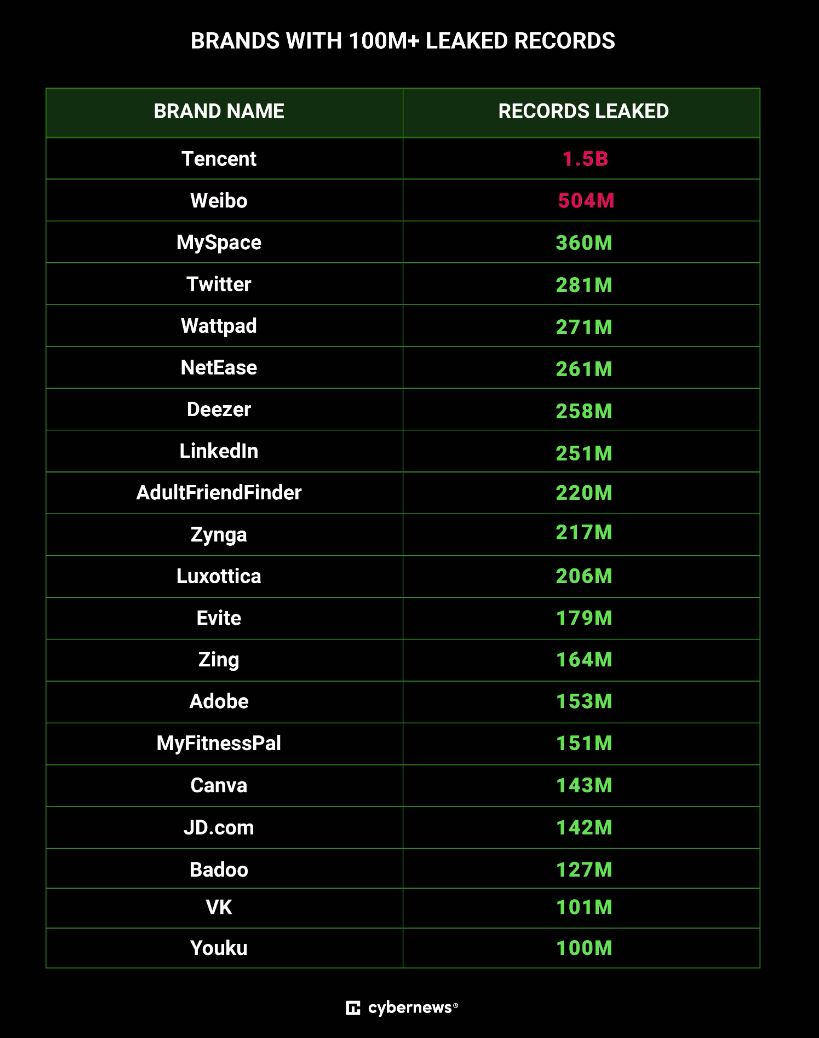
|
Data Breach | ★★★ | ||
| 2023-11-29 15:56:21 | Personne ne sait comment la société de pharmacie en ligne a été frappée par une violation de données impactant 2,3 millions de clients No One Knows How Online Pharmacy Company was Hit with a Data Breach Impacting 2.3 Million Customers (lien direct) |
Data Breach | ★★ | |||
| 2023-09-28 20:19:36 | L'industrie pharmaceutique constate une réduction des coûts de violation des données, mais a encore beaucoup à faire Pharma Industry Seeing Reduction in Data Breach Costs, But Still Have Much to Do (lien direct) |
Data Breach | ★★★ | |||
| 2023-09-20 12:10:03 | Les coûts de violation des données augmentent, mais les pros de la cybersécurité prennent toujours des risques Data Breach Costs Rise, But Cybersecurity Pros Still Take Risks (lien direct) |

|
Data Breach | ★★ | ||
| 2023-09-12 18:32:48 | AP StyleBook Bravel compromet les informations personnelles des clients AP Stylebook Data Breach Compromises Customer Personal Information (lien direct) |

|
Data Breach | ★★★ | ||
| 2023-08-23 12:58:54 | Les coûts de violation des données dans les soins de santé augmentent de 53% pour plus du double de la moyenne Data Breach Costs in Healthcare Rise 53% to More than Double the Average (lien direct) |

|
Data Breach | ★★★ | ||
| 2023-07-26 19:21:29 | Le nouveau rapport IBM révèle que le coût d'une violation de données dépasse désormais 4,45 millions de dollars New IBM report reveals the cost of a data breach now tops $4.45 million (lien direct) |
 IBM Security a publié son coût annuel d'un rapport de violation de données, révélant que le coût moyen mondial d'une violation de données a atteint 4,45 millions de dollars en 2023. Cela marque une augmentation significative de 15% au cours des 3 dernières années, faisant deC'est le coût le plus enregistré dans l'histoire du rapport.Notamment, les coûts de détection et d'escalade ont connu une augmentation substantielle de 42% au cours de la même période, indiquant un passage à des enquêtes de violation plus complexes.
IBM Security a publié son coût annuel d'un rapport de violation de données, révélant que le coût moyen mondial d'une violation de données a atteint 4,45 millions de dollars en 2023. Cela marque une augmentation significative de 15% au cours des 3 dernières années, faisant deC'est le coût le plus enregistré dans l'histoire du rapport.Notamment, les coûts de détection et d'escalade ont connu une augmentation substantielle de 42% au cours de la même période, indiquant un passage à des enquêtes de violation plus complexes.
 IBM Security has released its annual Cost of a Data Breach Report, revealing that the global average cost of a data breach reached $4.45 million in 2023. This marks a significant increase of 15% over the past 3 years, making it the highest recorded cost in the history of the report. Notably, detection and escalation costs have seen a substantial rise of 42% during the same period, indicating a shift towards more complex breach investigations.
IBM Security has released its annual Cost of a Data Breach Report, revealing that the global average cost of a data breach reached $4.45 million in 2023. This marks a significant increase of 15% over the past 3 years, making it the highest recorded cost in the history of the report. Notably, detection and escalation costs have seen a substantial rise of 42% during the same period, indicating a shift towards more complex breach investigations. |
Data Breach | ★★ | ||
| 2023-07-06 12:00:00 | Nerve Center: Protégez votre réseau contre les nouvelles souches de ransomware avec notre dernière mise à jour RANSIM Nerve Center: Protect Your Network Against New Ransomware Strains with Our Latest RanSim Update (lien direct) |
 ransomware continue d'être une menace majeure pour toutes les organisations et, selon le Verizon 2023 Data Breach Investigations Report , est toujours présent dans 24% des violations.
ransomware continue d'être une menace majeure pour toutes les organisations et, selon le Verizon 2023 Data Breach Investigations Report , est toujours présent dans 24% des violations.
 Ransomware continues to be a major threat for all organizations and, according to the Verizon 2023 Data Breach Investigations Report, is still present in 24% of breaches.
Ransomware continues to be a major threat for all organizations and, according to the Verizon 2023 Data Breach Investigations Report, is still present in 24% of breaches. |
Ransomware Data Breach Threat | ★★ | ||
| 2023-06-20 13:00:00 | Cyberheistnews Vol 13 # 25 [empreintes digitales partout] Les informations d'identification volées sont la cause profonde n ° 1 des violations de données CyberheistNews Vol 13 #25 [Fingerprints All Over] Stolen Credentials Are the No. 1 Root Cause of Data Breaches (lien direct) |
 CyberheistNews Vol 13 #25 | June 20th, 2023
[Fingerprints All Over] Stolen Credentials Are the No. 1 Root Cause of Data Breaches
Verizon\'s DBIR always has a lot of information to unpack, so I\'ll continue my review by covering how stolen credentials play a role in attacks.
This year\'s Data Breach Investigations Report has nearly 1 million incidents in their data set, making it the most statistically relevant set of report data anywhere.
So, what does the report say about the most common threat actions that are involved in data breaches? Overall, the use of stolen credentials is the overwhelming leader in data breaches, being involved in nearly 45% of breaches – this is more than double the second-place spot of "Other" (which includes a number of types of threat actions) and ransomware, which sits at around 20% of data breaches.
According to Verizon, stolen credentials were the "most popular entry point for breaches." As an example, in Basic Web Application Attacks, the use of stolen credentials was involved in 86% of attacks. The prevalence of credential use should come as no surprise, given the number of attacks that have focused on harvesting online credentials to provide access to both cloud platforms and on-premises networks alike.
And it\'s the social engineering attacks (whether via phish, vish, SMiSh, or web) where these credentials are compromised - something that can be significantly diminished by engaging users in security awareness training to familiarize them with common techniques and examples of attacks, so when they come across an attack set on stealing credentials, the user avoids becoming a victim.
Blog post with links:https://blog.knowbe4.com/stolen-credentials-top-breach-threat
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever l
CyberheistNews Vol 13 #25 | June 20th, 2023
[Fingerprints All Over] Stolen Credentials Are the No. 1 Root Cause of Data Breaches
Verizon\'s DBIR always has a lot of information to unpack, so I\'ll continue my review by covering how stolen credentials play a role in attacks.
This year\'s Data Breach Investigations Report has nearly 1 million incidents in their data set, making it the most statistically relevant set of report data anywhere.
So, what does the report say about the most common threat actions that are involved in data breaches? Overall, the use of stolen credentials is the overwhelming leader in data breaches, being involved in nearly 45% of breaches – this is more than double the second-place spot of "Other" (which includes a number of types of threat actions) and ransomware, which sits at around 20% of data breaches.
According to Verizon, stolen credentials were the "most popular entry point for breaches." As an example, in Basic Web Application Attacks, the use of stolen credentials was involved in 86% of attacks. The prevalence of credential use should come as no surprise, given the number of attacks that have focused on harvesting online credentials to provide access to both cloud platforms and on-premises networks alike.
And it\'s the social engineering attacks (whether via phish, vish, SMiSh, or web) where these credentials are compromised - something that can be significantly diminished by engaging users in security awareness training to familiarize them with common techniques and examples of attacks, so when they come across an attack set on stealing credentials, the user avoids becoming a victim.
Blog post with links:https://blog.knowbe4.com/stolen-credentials-top-breach-threat
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there\'s a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
The new PhishER Blocklist feature lets you use reported messages to prevent future malicious email with the same sender, URL or attachment from reaching other users. Now you can create a unique list of blocklist entries and dramatically improve your Microsoft 365 email filters without ever l |
Ransomware Data Breach Spam Malware Hack Vulnerability Threat Cloud | ChatGPT ChatGPT | ★★ | |
| 2023-05-09 13:00:00 | Cyberheistnews Vol 13 # 19 [Watch Your Back] Nouvelle fausse erreur de mise à jour Chrome Attaque cible vos utilisateurs CyberheistNews Vol 13 #19 [Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users (lien direct) |
 CyberheistNews Vol 13 #19 | May 9th, 2023
[Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users
Compromised websites (legitimate sites that have been successfully compromised to support social engineering) are serving visitors fake Google Chrome update error messages.
"Google Chrome users who use the browser regularly should be wary of a new attack campaign that distributes malware by posing as a Google Chrome update error message," Trend Micro warns. "The attack campaign has been operational since February 2023 and has a large impact area."
The message displayed reads, "UPDATE EXCEPTION. An error occurred in Chrome automatic update. Please install the update package manually later, or wait for the next automatic update." A link is provided at the bottom of the bogus error message that takes the user to what\'s misrepresented as a link that will support a Chrome manual update. In fact the link will download a ZIP file that contains an EXE file. The payload is a cryptojacking Monero miner.
A cryptojacker is bad enough since it will drain power and degrade device performance. This one also carries the potential for compromising sensitive information, particularly credentials, and serving as staging for further attacks.
This campaign may be more effective for its routine, innocent look. There are no spectacular threats, no promises of instant wealth, just a notice about a failed update. Users can become desensitized to the potential risks bogus messages concerning IT issues carry with them.
Informed users are the last line of defense against attacks like these. New school security awareness training can help any organization sustain that line of defense and create a strong security culture.
Blog post with links:https://blog.knowbe4.com/fake-chrome-update-error-messages
A Master Class on IT Security: Roger A. Grimes Teaches You Phishing Mitigation
Phishing attacks have come a long way from the spray-and-pray emails of just a few decades ago. Now they\'re more targeted, more cunning and more dangerous. And this enormous security gap leaves you open to business email compromise, session hijacking, ransomware and more.
Join Roger A. Grimes, KnowBe4\'s Data-Driven Defense Evangelist,
CyberheistNews Vol 13 #19 | May 9th, 2023
[Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users
Compromised websites (legitimate sites that have been successfully compromised to support social engineering) are serving visitors fake Google Chrome update error messages.
"Google Chrome users who use the browser regularly should be wary of a new attack campaign that distributes malware by posing as a Google Chrome update error message," Trend Micro warns. "The attack campaign has been operational since February 2023 and has a large impact area."
The message displayed reads, "UPDATE EXCEPTION. An error occurred in Chrome automatic update. Please install the update package manually later, or wait for the next automatic update." A link is provided at the bottom of the bogus error message that takes the user to what\'s misrepresented as a link that will support a Chrome manual update. In fact the link will download a ZIP file that contains an EXE file. The payload is a cryptojacking Monero miner.
A cryptojacker is bad enough since it will drain power and degrade device performance. This one also carries the potential for compromising sensitive information, particularly credentials, and serving as staging for further attacks.
This campaign may be more effective for its routine, innocent look. There are no spectacular threats, no promises of instant wealth, just a notice about a failed update. Users can become desensitized to the potential risks bogus messages concerning IT issues carry with them.
Informed users are the last line of defense against attacks like these. New school security awareness training can help any organization sustain that line of defense and create a strong security culture.
Blog post with links:https://blog.knowbe4.com/fake-chrome-update-error-messages
A Master Class on IT Security: Roger A. Grimes Teaches You Phishing Mitigation
Phishing attacks have come a long way from the spray-and-pray emails of just a few decades ago. Now they\'re more targeted, more cunning and more dangerous. And this enormous security gap leaves you open to business email compromise, session hijacking, ransomware and more.
Join Roger A. Grimes, KnowBe4\'s Data-Driven Defense Evangelist, |
Ransomware Data Breach Spam Malware Tool Threat Prediction | NotPetya NotPetya APT 28 ChatGPT ChatGPT | ★★ | |
| 2023-04-11 13:16:54 | Cyberheistnews Vol 13 # 15 [Le nouveau visage de la fraude] FTC fait la lumière sur les escroqueries d'urgence familiale améliorées AI-AI CyberheistNews Vol 13 #15 [The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams (lien direct) |
 CyberheistNews Vol 13 #15 | April 11th, 2023
[The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams
The Federal Trade Commission is alerting consumers about a next-level, more sophisticated family emergency scam that uses AI which imitates the voice of a "family member in distress."
They started out with: "You get a call. There\'s a panicked voice on the line. It\'s your grandson. He says he\'s in deep trouble - he wrecked the car and landed in jail. But you can help by sending money. You take a deep breath and think. You\'ve heard about grandparent scams. But darn, it sounds just like him. How could it be a scam? Voice cloning, that\'s how."
"Don\'t Trust The Voice"
The FTC explains: "Artificial intelligence is no longer a far-fetched idea out of a sci-fi movie. We\'re living with it, here and now. A scammer could use AI to clone the voice of your loved one. All he needs is a short audio clip of your family member\'s voice - which he could get from content posted online - and a voice-cloning program. When the scammer calls you, he\'ll sound just like your loved one.
"So how can you tell if a family member is in trouble or if it\'s a scammer using a cloned voice? Don\'t trust the voice. Call the person who supposedly contacted you and verify the story. Use a phone number you know is theirs. If you can\'t reach your loved one, try to get in touch with them through another family member or their friends."
Full text of the alert is at the FTC website. Share with friends, family and co-workers:https://blog.knowbe4.com/the-new-face-of-fraud-ftc-sheds-light-on-ai-enhanced-family-emergency-scams
A Master Class on IT Security: Roger A. Grimes Teaches Ransomware Mitigation
Cybercriminals have become thoughtful about ransomware attacks; taking time to maximize your organization\'s potential damage and their payoff. Protecting your network from this growing threat is more important than ever. And nobody knows this more than Roger A. Grimes, Data-Driven Defense Evangelist at KnowBe4.
With 30+ years of experience as a computer security consultant, instructor, and award-winning author, Roger has dedicated his life to making
CyberheistNews Vol 13 #15 | April 11th, 2023
[The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams
The Federal Trade Commission is alerting consumers about a next-level, more sophisticated family emergency scam that uses AI which imitates the voice of a "family member in distress."
They started out with: "You get a call. There\'s a panicked voice on the line. It\'s your grandson. He says he\'s in deep trouble - he wrecked the car and landed in jail. But you can help by sending money. You take a deep breath and think. You\'ve heard about grandparent scams. But darn, it sounds just like him. How could it be a scam? Voice cloning, that\'s how."
"Don\'t Trust The Voice"
The FTC explains: "Artificial intelligence is no longer a far-fetched idea out of a sci-fi movie. We\'re living with it, here and now. A scammer could use AI to clone the voice of your loved one. All he needs is a short audio clip of your family member\'s voice - which he could get from content posted online - and a voice-cloning program. When the scammer calls you, he\'ll sound just like your loved one.
"So how can you tell if a family member is in trouble or if it\'s a scammer using a cloned voice? Don\'t trust the voice. Call the person who supposedly contacted you and verify the story. Use a phone number you know is theirs. If you can\'t reach your loved one, try to get in touch with them through another family member or their friends."
Full text of the alert is at the FTC website. Share with friends, family and co-workers:https://blog.knowbe4.com/the-new-face-of-fraud-ftc-sheds-light-on-ai-enhanced-family-emergency-scams
A Master Class on IT Security: Roger A. Grimes Teaches Ransomware Mitigation
Cybercriminals have become thoughtful about ransomware attacks; taking time to maximize your organization\'s potential damage and their payoff. Protecting your network from this growing threat is more important than ever. And nobody knows this more than Roger A. Grimes, Data-Driven Defense Evangelist at KnowBe4.
With 30+ years of experience as a computer security consultant, instructor, and award-winning author, Roger has dedicated his life to making |
Ransomware Data Breach Spam Malware Hack Tool Threat | ChatGPT ChatGPT | ★★ | |
| 2023-04-11 12:00:00 | [Outil gratuit] Voir quels utilisateurs sont susceptibles de se faire un comportement de sécurité risqué avec l'aperçu gratuit de SecurityCoach! [Free Tool] See Which Users Are Susceptible to Risky Security Behavior with SecurityCoach Free Preview! (lien direct) |
Data Breach Hack | ★★ | |||
| 2023-04-03 18:32:00 | Latitude forcée d'arrêter d'ajouter de nouveaux clients à la suite de la violation Latitude Forced To Stop Adding New Customers in Aftermath of Breach (lien direct) |
Data Breach Threat | ★★ | |||
| 2023-03-14 13:00:00 | CyberheistNews Vol 13 #11 [Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears (lien direct) |
 CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl
CyberheistNews Vol 13 #11 | March 14th, 2023
[Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put sensitive corporate data into the large language model, raising concerns that its popularity may result in massive leaks of proprietary information. Yikes.
I'm giving you a short extract of the story and the link to the whole article is below.
"Employees are submitting sensitive business data and privacy-protected information to large language models (LLMs) such as ChatGPT, raising concerns that artificial intelligence (AI) services could be incorporating the data into their models, and that information could be retrieved at a later date if proper data security isn't in place for the service.
"In a recent report, data security service Cyberhaven detected and blocked requests to input data into ChatGPT from 4.2% of the 1.6 million workers at its client companies because of the risk of leaking confidential info, client data, source code, or regulated information to the LLM.
"In one case, an executive cut and pasted the firm's 2023 strategy document into ChatGPT and asked it to create a PowerPoint deck. In another case, a doctor input his patient's name and their medical condition and asked ChatGPT to craft a letter to the patient's insurance company.
"And as more employees use ChatGPT and other AI-based services as productivity tools, the risk will grow, says Howard Ting, CEO of Cyberhaven.
"'There was this big migration of data from on-prem to cloud, and the next big shift is going to be the migration of data into these generative apps," he says. "And how that plays out [remains to be seen] - I think, we're in pregame; we're not even in the first inning.'"
Your employees need to be stepped through new-school security awareness training so that they understand the risks of doing things like this.
Blog post with links:https://blog.knowbe4.com/employees-are-feeding-sensitive-biz-data-to-chatgpt-raising-security-fears
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blockl |
Ransomware Data Breach Spam Malware Threat Guideline Medical | ChatGPT ChatGPT | ★★ | |
| 2023-02-21 14:00:00 | CyberheistNews Vol 13 #08 [Heads Up] Reddit Is the Latest Victim of a Spear Phishing Attack Resulting in a Data Breach (lien direct) |
 CyberheistNews Vol 13 #08 | February 21st, 2023
[Heads Up] Reddit Is the Latest Victim of a Spear Phishing Attack Resulting in a Data Breach
There is a lot to learn from Reddit's recent data breach, which was the result of an employee falling for a "sophisticated and highly-targeted" spear phishing attack.
I spend a lot of time talking about phishing attacks and the specifics that closely surround that pivotal action taken by the user once they are duped into believing the phishing email was legitimate.
However, there are additional details about the attack we can analyze to see what kind of access the attacker was able to garner from this attack. But first, here are the basics:
According to Reddit, an attacker set up a website that impersonated the company's intranet gateway, then sent targeted phishing emails to Reddit employees. The site was designed to steal credentials and two-factor authentication tokens.
There are only a few details from the breach, but the notification does mention that the threat actor was able to access "some internal docs, code, as well as some internal dashboards and business systems."
Since the notice does imply that only a single employee fell victim, we have to make a few assumptions about this attack:
The attacker had some knowledge of Reddit's internal workings – The fact that the attacker can spoof an intranet gateway shows they had some familiarity with the gateway's look and feel, and its use by Reddit employees.
The targeting of victims was limited to users with specific desired access – Given the knowledge about the intranet, it's reasonable to believe that the attacker(s) targeted users with specific roles within Reddit. From the use of the term "code," I'm going to assume the target was developers or someone on the product side of Reddit.
The attacker may have been an initial access broker – Despite the access gained that Reddit is making out to be not a big deal, they do also mention that no production systems were accessed. This makes me believe that this attack may have been focused on gaining a foothold within Reddit versus penetrating more sensitive systems and data.
There are also a few takeaways from this attack that you can learn from:
2FA is an important security measure – Despite the fact that the threat actor collected and (I'm guessing) passed the credentials and 2FA details onto the legitimate Intranet gateway-a classic man-in-the
CyberheistNews Vol 13 #08 | February 21st, 2023
[Heads Up] Reddit Is the Latest Victim of a Spear Phishing Attack Resulting in a Data Breach
There is a lot to learn from Reddit's recent data breach, which was the result of an employee falling for a "sophisticated and highly-targeted" spear phishing attack.
I spend a lot of time talking about phishing attacks and the specifics that closely surround that pivotal action taken by the user once they are duped into believing the phishing email was legitimate.
However, there are additional details about the attack we can analyze to see what kind of access the attacker was able to garner from this attack. But first, here are the basics:
According to Reddit, an attacker set up a website that impersonated the company's intranet gateway, then sent targeted phishing emails to Reddit employees. The site was designed to steal credentials and two-factor authentication tokens.
There are only a few details from the breach, but the notification does mention that the threat actor was able to access "some internal docs, code, as well as some internal dashboards and business systems."
Since the notice does imply that only a single employee fell victim, we have to make a few assumptions about this attack:
The attacker had some knowledge of Reddit's internal workings – The fact that the attacker can spoof an intranet gateway shows they had some familiarity with the gateway's look and feel, and its use by Reddit employees.
The targeting of victims was limited to users with specific desired access – Given the knowledge about the intranet, it's reasonable to believe that the attacker(s) targeted users with specific roles within Reddit. From the use of the term "code," I'm going to assume the target was developers or someone on the product side of Reddit.
The attacker may have been an initial access broker – Despite the access gained that Reddit is making out to be not a big deal, they do also mention that no production systems were accessed. This makes me believe that this attack may have been focused on gaining a foothold within Reddit versus penetrating more sensitive systems and data.
There are also a few takeaways from this attack that you can learn from:
2FA is an important security measure – Despite the fact that the threat actor collected and (I'm guessing) passed the credentials and 2FA details onto the legitimate Intranet gateway-a classic man-in-the |
Data Breach Hack Threat Guideline | ChatGPT | ★★ | |
| 2023-02-15 13:18:20 | Reddit is the Latest Victim of a Spear Phishing Attack Resulting in a Data Breach (lien direct) |

|
Data Breach | ★★ | ||
| 2022-12-06 14:30:00 | CyberheistNews Vol 12 #49 [Keep An Eye Out] Beware of New Holiday Gift Card Scams (lien direct) |
 CyberheistNews Vol 12 #49 | December 6th, 2022
[Keep An Eye Out] Beware of New Holiday Gift Card Scams
By Roger A. Grimes
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something.
The gift card market is estimated in the many hundreds of BILLIONS of dollars. Who doesn't like to get a free gift card? Unfortunately, scammers often use gift cards as a way to steal value from their victims. There are dozens of ways gift cards can be used by scammers to steal money.
Roger covers these three scams in a short [VIDEO] and in detail on the KnowBe4 blog:
You Need to Pay a Bill Using Gift Cards
Maliciously Modified Gift Cards in Stores
Phish You for Information to Supposedly Get a Gift Card
Blog post with 2:13 [VIDEO] and links you can share with your users and family:https://blog.knowbe4.com/beware-of-holiday-gift-card-scams
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, December 7 @ 2:00 PM (ET), for a live demo of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! KnowBe4 Mobile Learner App - Users Can Now Train Anytime, Anywhere!
NEW! Security Culture Benchmarking feature lets you compare your organization's security culture with your peers
NEW! AI-Driven phishing and training recommendations for your end users
Did You Know? You can upload your own training video and SCORM modules into your account for home workers
Active Directory or SCIM Integration to easily upload user data, eliminating the need to manually manage user changes
Find out how 50,000+ organizations have mobilized their end-users as their human firewall.
Date/Time: TOMORROW, Wednesday, December 7 @ 2:00 PM (ET)
Save My Spot!https://event.on24.com/wcc/r/3947028/0273119CCBF116DBE42DF81F151FF99F?partnerref=CHN3
CyberheistNews Vol 12 #49 | December 6th, 2022
[Keep An Eye Out] Beware of New Holiday Gift Card Scams
By Roger A. Grimes
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, easy to use, easy to gift, usually allow the receiver to pick just what they want, and are often received as a reward for doing something.
The gift card market is estimated in the many hundreds of BILLIONS of dollars. Who doesn't like to get a free gift card? Unfortunately, scammers often use gift cards as a way to steal value from their victims. There are dozens of ways gift cards can be used by scammers to steal money.
Roger covers these three scams in a short [VIDEO] and in detail on the KnowBe4 blog:
You Need to Pay a Bill Using Gift Cards
Maliciously Modified Gift Cards in Stores
Phish You for Information to Supposedly Get a Gift Card
Blog post with 2:13 [VIDEO] and links you can share with your users and family:https://blog.knowbe4.com/beware-of-holiday-gift-card-scams
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human firewall as your last line of defense.
Join us TOMORROW, Wednesday, December 7 @ 2:00 PM (ET), for a live demo of how KnowBe4 introduces a new-school approach to security awareness training and simulated phishing.
Get a look at THREE NEW FEATURES and see how easy it is to train and phish your users.
NEW! KnowBe4 Mobile Learner App - Users Can Now Train Anytime, Anywhere!
NEW! Security Culture Benchmarking feature lets you compare your organization's security culture with your peers
NEW! AI-Driven phishing and training recommendations for your end users
Did You Know? You can upload your own training video and SCORM modules into your account for home workers
Active Directory or SCIM Integration to easily upload user data, eliminating the need to manually manage user changes
Find out how 50,000+ organizations have mobilized their end-users as their human firewall.
Date/Time: TOMORROW, Wednesday, December 7 @ 2:00 PM (ET)
Save My Spot!https://event.on24.com/wcc/r/3947028/0273119CCBF116DBE42DF81F151FF99F?partnerref=CHN3
|
Ransomware Data Breach Spam Hack Tool Guideline | ★★★ | ||
| 2022-11-26 20:29:06 | WhatsApp data breach sees nearly 500 million user records up for sale (lien direct) |

|
Data Breach | ★★ | ||
| 2022-09-26 14:00:46 | Recent Optus Data Breach Teaches the Importance of Recognizing Social Engineering (lien direct) |

|
Data Breach | |||
| 2022-08-03 12:50:01 | New Data Breach Extortion Attack Begins with a Fake Duolingo or MasterClass Subscription Scam (lien direct) |

|
Data Breach | |||
| 2022-07-12 13:21:14 | (Déjà vu) CyberheistNews Vol 12 #28 [Eye Opener] Lessons Learned From a Big Hotel\'s Recent Data Breach Caused by Social Engineering (lien direct) |

|
Data Breach | |||
| 2022-07-08 12:55:07 | Lessons Learned from a Popular Hotel\'s Recent Data Breach Involving Social Engineering (lien direct) |

|
Data Breach | |||
| 2022-06-01 12:59:33 | CyberheistNews Vol 12 #22 [Heads Up] The New Verizon 2022 Data Breach Investigation Report Shows Sharp Rise in Ransomware (lien direct) |

|
Ransomware Data Breach | |||
| 2022-05-12 16:23:17 | Trezor Crypto Wallet Attacks Results in Class Action Lawsuit Against MailChimp Owner Intuit (lien direct) |
 Months after the MailChimp data breach targeting 102 companies in the crypto sector, a new lawsuit has been filed seeking millions of dollars in damages.
Months after the MailChimp data breach targeting 102 companies in the crypto sector, a new lawsuit has been filed seeking millions of dollars in damages. |
Data Breach | ★★★ | ||
| 2022-03-02 18:32:16 | Data Breach Volumes in the U.S. Grow by 10% in 2021 (lien direct) |
 New data shows despite decreases in global data breach levels (-5%) in 2021, the U.S. experienced proportionally more data breaches than in the previous year.
New data shows despite decreases in global data breach levels (-5%) in 2021, the U.S. experienced proportionally more data breaches than in the previous year. |
Data Breach | |||
| 2022-02-15 14:24:51 | CyberheistNews Vol 12 #07 [Heads Up] FBI Warns Against New Criminal QR Code Scams (lien direct) |
 [Heads Up] FBI Warns Against New Criminal QR Code Scams
Email not displaying? |
CyberheistNews Vol 12 #07 | Feb. 15th., 2022
[Heads Up] FBI Warns Against New Criminal QR Code Scams
QR codes have been around for many years. While they were adopted for certain niche uses, they never did quite reach their full potential. They are a bit like Rick Astley in that regard, really popular for one song, but well after the boat had sailed. Do not get me wrong, Rick Astley achieved a lot. In recent years, he has become immortalized as a meme and Rick roller, but he could have been so much more.
However, in recent years, with lockdown and the drive to keep things at arms length, QR codes have become an efficient way to facilitate contactless communications, or the transfer of offers without physically handing over a coupon. As this has grown in popularity, more people have become familiar with how to generate their own QR codes and how to use them as virtual business cards, discount codes, links to videos and all sorts of other things.
QRime Codes
As with most things, once they begin to gain a bit of popularity, criminals move in to see how they can manipulate the situation to their advantage. Recently, we have seen fake QR codes stuck to parking meters enticing unwitting drivers to scan the code, and hand over their payment details believing they were paying for parking, whereas they were actually handing over their payment information to criminals.
The rise in QR code fraud resulted in the FBI releasing an advisory warning against fake QR codes that are being used to scam users. In many cases, a fake QR code will lead people to a website that looks like the intended legitimate site. So, the usual verification process of checking the URL and any other red flags apply.
CONTINUED with links and 4 example malicious QR codes on the KnowBe4 blog:
https://blog.knowbe4.com/qr-codes-in-the-time-of-cybercrime
[Heads Up] FBI Warns Against New Criminal QR Code Scams
Email not displaying? |
CyberheistNews Vol 12 #07 | Feb. 15th., 2022
[Heads Up] FBI Warns Against New Criminal QR Code Scams
QR codes have been around for many years. While they were adopted for certain niche uses, they never did quite reach their full potential. They are a bit like Rick Astley in that regard, really popular for one song, but well after the boat had sailed. Do not get me wrong, Rick Astley achieved a lot. In recent years, he has become immortalized as a meme and Rick roller, but he could have been so much more.
However, in recent years, with lockdown and the drive to keep things at arms length, QR codes have become an efficient way to facilitate contactless communications, or the transfer of offers without physically handing over a coupon. As this has grown in popularity, more people have become familiar with how to generate their own QR codes and how to use them as virtual business cards, discount codes, links to videos and all sorts of other things.
QRime Codes
As with most things, once they begin to gain a bit of popularity, criminals move in to see how they can manipulate the situation to their advantage. Recently, we have seen fake QR codes stuck to parking meters enticing unwitting drivers to scan the code, and hand over their payment details believing they were paying for parking, whereas they were actually handing over their payment information to criminals.
The rise in QR code fraud resulted in the FBI releasing an advisory warning against fake QR codes that are being used to scam users. In many cases, a fake QR code will lead people to a website that looks like the intended legitimate site. So, the usual verification process of checking the URL and any other red flags apply.
CONTINUED with links and 4 example malicious QR codes on the KnowBe4 blog:
https://blog.knowbe4.com/qr-codes-in-the-time-of-cybercrime
|
Ransomware Data Breach Spam Malware Threat Guideline | APT 15 APT 43 | ||
| 2021-12-28 18:28:54 | West Virginia Healthcare Breach Traced to Phishing (lien direct) |
 Monongalia Health System in West Virginia has disclosed a data breach that exposed sensitive patient and employee information.
Monongalia Health System in West Virginia has disclosed a data breach that exposed sensitive patient and employee information. |
Data Breach | |||
| 2021-12-13 14:09:38 | Socially Engineering Your Way to Customer Data (lien direct) |
 US telecommunications company Cox Communications has disclosed a data breach that exposed some customers' information, BleepingComputer reports. The company said in a breach notification letter that an attacker was able to gain access to some customer accounts after using social engineering tactics to impersonate a Cox employee.
US telecommunications company Cox Communications has disclosed a data breach that exposed some customers' information, BleepingComputer reports. The company said in a breach notification letter that an attacker was able to gain access to some customer accounts after using social engineering tactics to impersonate a Cox employee. |
Data Breach | |||
| 2021-12-07 15:53:12 | Victims: After a Data Breach, Changing Passwords and Good Password Hygiene Remain Unimportant (lien direct) |
 New shocking data shows how unconcerned victim users are after being notified of a data breach involving their credentials, personal information, and even social media accounts.
New shocking data shows how unconcerned victim users are after being notified of a data breach involving their credentials, personal information, and even social media accounts. |
Data Breach |
1
We have: 31 articles.
We have: 31 articles.
To see everything:
Our RSS (filtrered)
